Asymmetric Cryptography Systems Are Which of the Following
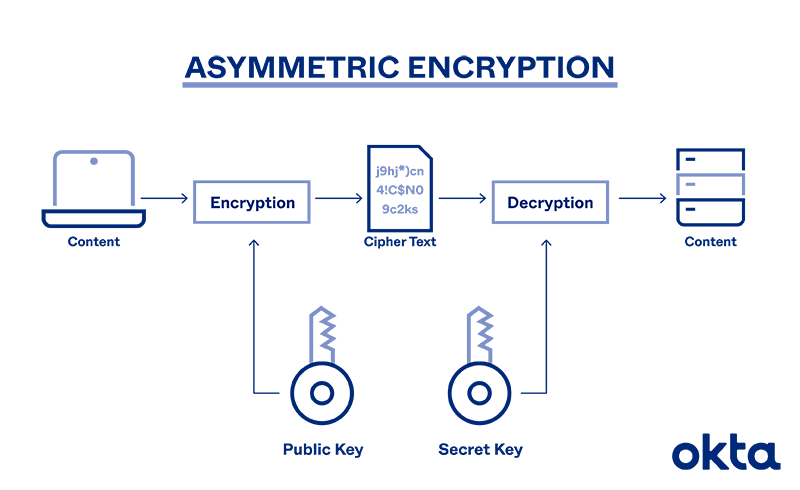
Asymmetric Encryption consists of two cryptographic keys known as Public Key and Private Key. In general there are three types Of cryptography.

Asymmetric Cryptography An Overview Sciencedirect Topics
The Correct Answer is-D.
. Due to this it is usually utilized in smaller transactions usually to establish safe communication channels or authenticating users. Asymmetric encryption is also referred to as which of the following. First the sender obtains the receivers public key.
Asymmetric encryption systems use two keys public and private C. 128 or 256-bit key size. Trusted Platform Module TPM B.
It uses one single key for encrypting a message as well as decrypting it. A Hub B Key C Public key D Certificate authority Show Answer. Cryptography or cryptology from Ancient Greek.
The same speed as symmetric cryptography systemsd. The recipient of a message encrypted with a key must have a copy of the same key to decrypt the message. It is smaller than or equal to the size of the original plain text.
Hardware Security Module HSM 20. Asymmetric cryptography involves a pair of keys to encrypt and decrypt data. Asymmetric cryptography systems are which of the followinga.
Which of the following statements is true. Asymmetric encryption on the other hand requires the use of two separate keys ie a public key and a private key. RSA 2048-bit or higher key size.
More generally cryptography is about constructing and analyzing protocols that prevent third. The two participants in the asymmetric encryption workflow are the sender and the receiver. A single key is used and is transferred using a key management system d.
Each user has two keys. It only provides confidentiality. A symmetric algorithm that operates on plaintext one bit at a time.
Public key encryption is by far the most common type of asymmetric cryptography. Which of the following ideasmovements were invented AFTER the Bitcoin network went live. Much safer as two keys are involved in encryption and decryption.
Faster than symmetric cryptography systemsb. Self-encrypting hard disk drives HDDs C. What is the difference between a hard and a.
Asymmetric encryption is faster than symmetric encryption but cannot. Which of the following has an onboard key generator and key storage facility accelerated symmetric and asymmetric encryption and can back up sensitive material in encrypted form. The method of hiding data in plain view in pictures graphics or text.
The encryption process is slow. Types Of Cryptography. In this system each user has two keys a public key and a private key.
The keys are simply large numbers that are paired together. It uses two different keys- one for encryption and another for decryption of a message. A Shared key B Public key.
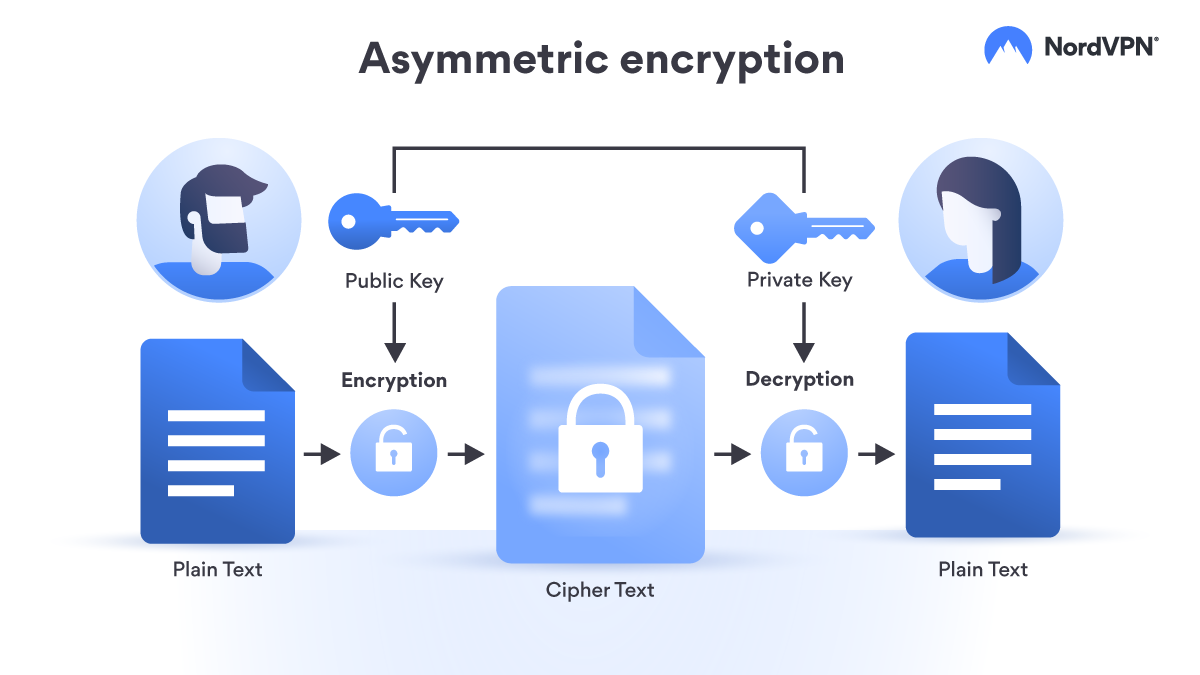
The public key is used to encrypt a message sent to the private key owner c. Symmetric vs Asymmetric Encryption. Asymmetric cryptography is a type of encryption where the key used to encrypt the information is not the same as the key used to decrypt the information.
An encryption algorithm that uses only one key to encrypt and decrypt data. Both keys are mathematically related both. Symmetric Encryption is a lot quicker compared to the Asymmetric method.
In symmetric key encryption resource utilization is low as compared to asymmetric key encryption. Which of the following manages digital certificates. Encrypted hardware-based USB devices.
In asymmetric key cryptography the private key is kept by one public key and one private key to prevent unauthorized entry or usage. Asymmetric cryptography is scalable for use in very large and ever expanding environments where data are frequently exchanged between different communication partners. A shared key is used to encrypt all messages and the private key decrypts them b.
Asymmetric encryption requires high consumption of resources. It is an encryption system where the sender and receiver of message use a single common key to encrypt and decrypt messages. Asymmetric cryptography which can also be called public-key cryptography uses private and public keys to encrypt and decrypt the data.
Anybody can use a public key to encrypt a. LOCALIZAÇÃO Rua Augusto Corrêa 001 UFPA PIEBT Módulo 06 55 91 3201-8023 ramal 212. It is used when a large amount of data is required to transfer.
Each has its own pair of public and private keys. Less secured due to use a single key for encryption. Which of the following is true about asymmetric cryptography.
A public and private key system differs from symmetric because it uses which of the following. And γράφειν graphein to write or -λογία-logia study respectively is the practice and study of techniques for secure communication in the presence of adversarial behavior. Asymmetric cryptography better known as public-key cryptography encrypts and decrypts a message using a pair of similar keys.
Symmetric Key Encryption. Public-key cryptography or asymmetric cryptography is a cryptographic system that uses pairs of keysEach pair consists of a public key which may be known to others and a private key which may not be known by anyone except the owner. Asymmetric Key Encryption.
The generation of such key pairs depends on cryptographic algorithms which are based on mathematical problems termed one-way. It is used to transfer small amount of data. Hands-On Ethical Hacking and Network Defense 2nd Edition Edit edition Solutions for Chapter 12 Problem 17RQ.
Public Key is One of the keys in the pair that can be shared with everyone whereas Private key is. Encryption types can be easily divided into these two categories. In this case data can be encoded by the public key.
A Asymmetric cryptography B The cypherpunk movement I do not want to answer this question D None of the options listed E Distributed networks חד F Proof-of-work 10. However they are asymmetric means not identical. The primary difference between these two types of encryption is that with Symmetric encryption the message to be protected can be encrypted and decrypted using the same key.
It provides confidentiality authenticity and non-repudiation. Symmetric key encryption works on low usage of resources. As Asymmetric Encryption incorporates two separate keys the process is slowed down considerably.
Asymmetric cryptography is a second form of cryptography. Slower than symmetric cryptography systemsc. Next the plaintext message is encrypted by the sender using the receiver.
Naturally asymmetric is a more advanced encryption standard and thus is slower and resource-consuming. The private key can be used to encrypt and decrypt a message The. Computer Science questions and answers.
Symmetric encryption is faster than asymmetric encryption. Symmetric encryption consists of one of key for encryption and decryption. Symmetric Key Systems are faster and simpler but the problem is that sender and receiver have to somehow exchange.
A public key and a private key.
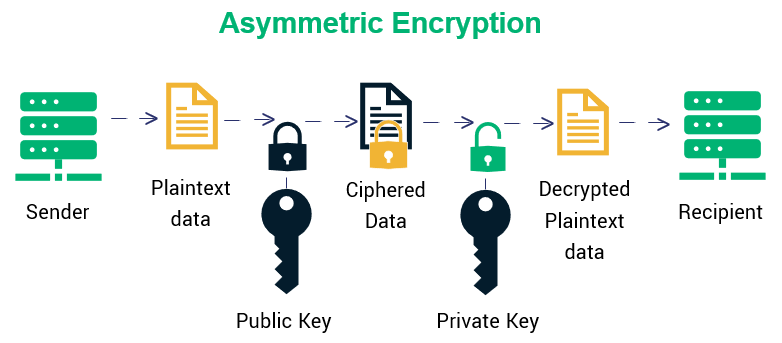
Types Of Encryption What To Know About Symmetric Vs Asymmetric Encryption Infosec Insights

Si110 Asymmetric Public Key Cryptography
Comments
Post a Comment